What Is Ransomware and Why You Should Be Concerned
Oct 20, 2020 by Robert Gravelle
Ransomware attacks are nothing new. In fact, the first known ransomware virus was created in 1989! So why bring them up now? While the frequency of ransomware attacks has fluctuated over the years, recent statistics show that ransomware attacks rose significantly in frequency in 2019 and won’t be letting up any time soon. For that reason, you should know what ransomware attacks are, how they work, and how best to deter malicious entities from targeting your organization. And that is exactly what you’ll learn here today!
Ransomware attacks typically use much the same tricks to gain access to your server(s) as other hacking attacks. For instance, a phishing attack in the form of an e-mail with an infected attachment may be sent to employees of an organization. All it takes is for one user to open the attachment to allow the ransomware to execute on the network. Once inside your network, the ransomware immediately begins to encrypt files on the target system. Moreover, the malicious software may also attempt to encrypt files on any mapped drives or network-connected device that the infected machine has write permission to. In the case of databases, the database file may be encrypted. It’s where the database schema and data are stored on the hard drive. What’s worse, not only do your data and log files become unreadable, but you can even lose access to your backups. Once your backups are encrypted, you (and your entire organization) may be at the mercy of the attacker(s)!
Once the database file has been encrypted, someone will be contacted by the attacker(s), or the server will respond to requests asking for payment in the form of Bitcoin for a key to decrypt the files.

The old sports adage that “the best defence is a good offense” holds just as true for cyberattacks. One would hope that your organization maintains a strong firewall that keeps as many malicious emails out of employees’ hands as possible. Users also play a vital role as guardians of the organization’s infrastructure. As such, it is every employee’s responsibility to only open attachments who’s contents they know are safe. Even family and friends cannot be completely trusted, as their email accounts may be hacked.
So, what can Database Administrators (DBA) do to help bolster security?
Quite a lot, actually.
In many instances, ransomware attack have capitalized on an unpatched vulnerability. Upon reviewing the thousands of MySQL ransomware attacks a few years ago, investigators determined that the underlying security weakness in the vast majority of cases was either gaping holes in security protocols or even an almost complete lack thereof! The good news is that you can prevent being a victim of many ransomware attacks simply by installing the latest security patches as soon as they are released.
System administrators of MariaDB, MySQL, and SQL Server can help protect their server instances by monitoring performance on a regular basis. Navicat Monitor is the best way to always know exactly what is happening on your database servers. Monitoring is especially effective in cases where hackers make tentative intrusions into systems to ascertain the best targets on which to introduce their malware. Vigilant monitoring helps highlight unusual system activity so it can be addressed by database administrators and security personnel.
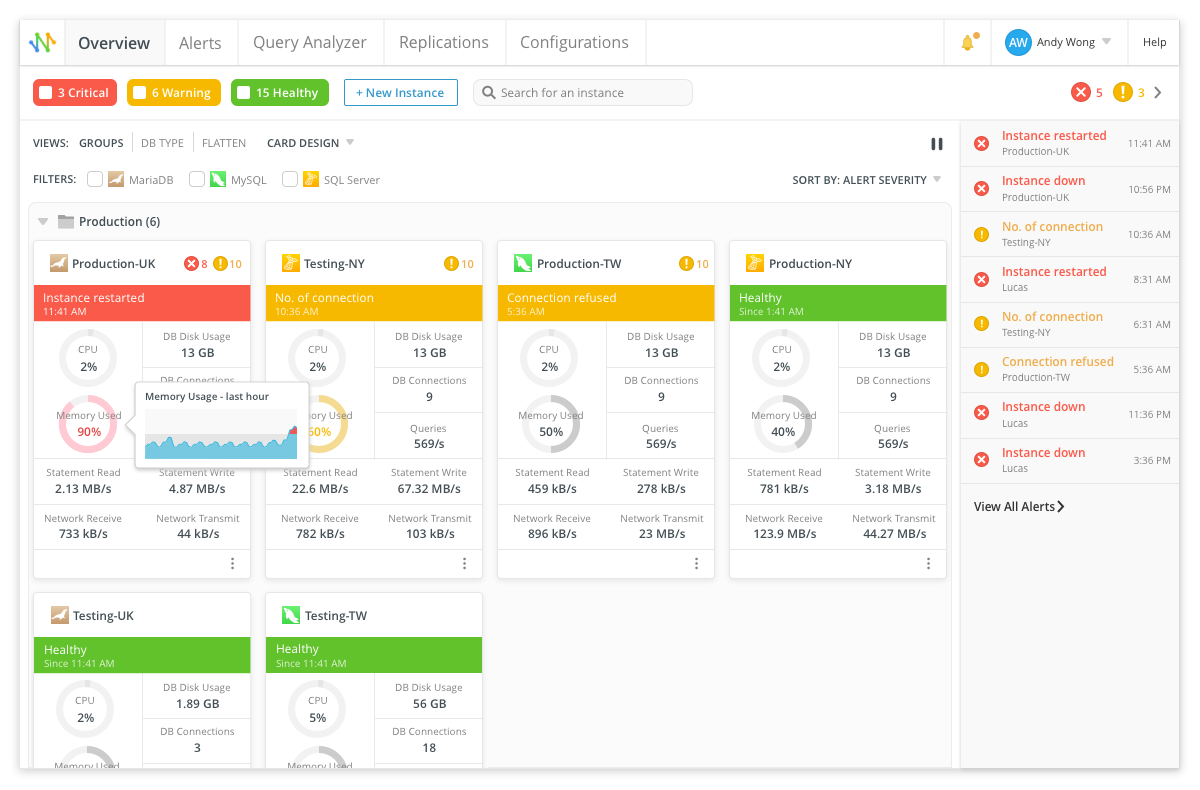
With ransomware attacks on the rise in 2020, now is the time to take steps to protect your data and organization. Navicat Monitor helps catch suspicious activity before your database is compromised!